For many enterprises, ordering the development of custom software is the best, and in some cases the only, option to obtain a system that will be fully tailored to their individual needs.
However, we should be aware that the specificity of this type of software also results in additional challenges, especially in terms of security, which must be taken into account not only by the software house, but also by the Client.
In this article, we will try to explain both the most common causes of data security breaches in custom systems, as well as how to protect yourself against them, using the examples of our best practices.
How we define software security?
Software security is a set of practices to protect the system and the data processed in it against unauthorized access, use or destruction.
Appropriately selected software security solutions help ensure that data is protected during transfer and storage, and can help protect against ransomware and other types of malware exploiting possible vulnerabilities in the system.
Why the security aspect is important in the process of creating custom software?
One of the main reasons why attention to security is essential when creating custom software is the protection of confidential data. Business systems often store and process sensitive information such as personal data, financial records and trade secrets.
If this information falls into the wrong hands, it can lead to serious consequences such as identity theft, financial loss, and damage to your company reputation. Therefore, developers must guarantee an appropriate level of security of the delivered systems in order to protect this data.
Another reason why the security aspect is crucial in the development of custom software is the prevention of cyberattacks. Cybercriminals are constantly refining their tactics, making it difficult for businesses to keep up with the latest threats. Custom software that lacks proper security measures can be an easy target for cybercriminals who want to exploit vulnerabilities and gain unauthorized access to systems.
Another aspect affecting the need to properly secure custom systems is the requirement to ensure compliance with local and international regulations.
Many industries have strict data protection and privacy regulations, such as HIPAA for healthcare or GDPR for companies operating in the European Union. Failure to comply with these laws can result in significant fines and legal consequences. Therefore, developers must ensure that their custom software solutions meet these legal requirements by implementing appropriate security measures.

What are the most common causes of data breaches?
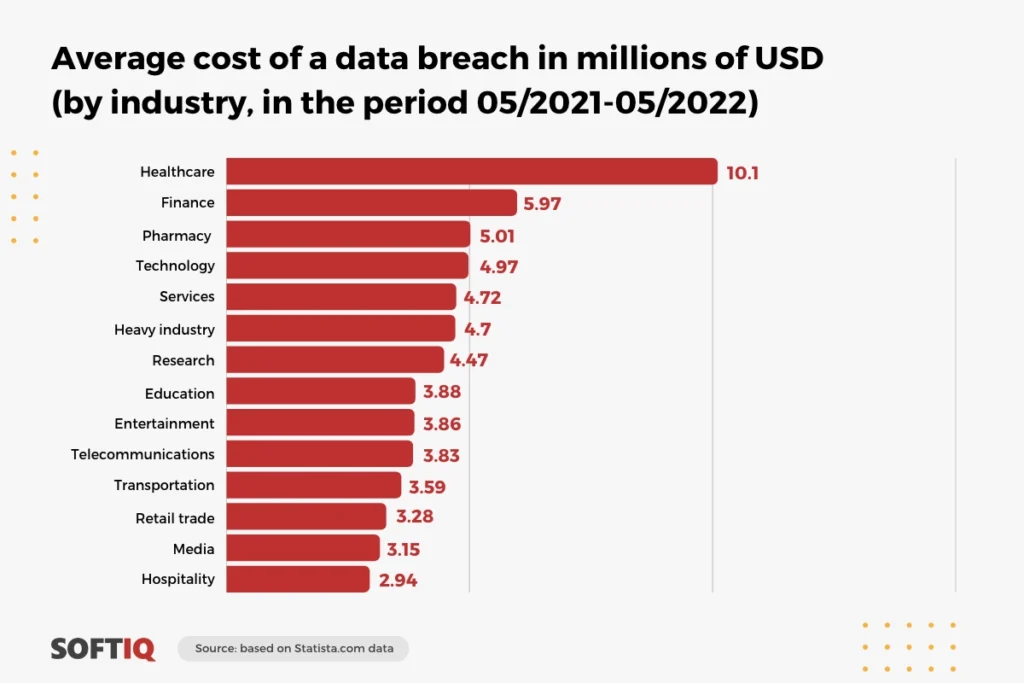
Data breaches are a serious concern for organizations, especially those dealing with sensitive or confidential information. The financial consequences for many companies can be significant – for example, according to a report prepared by Statista.com, the average cost of a data security breach in the period from March 2021 to March 2022 for entities operating in the healthcare sector reached USD 10.1 million.
Custom software can be particularly susceptible to data breaches due to its unique nature and potential vulnerabilities.
There are several most common causes of data breaches in the case of custom software:
1. Shortcomings in software design and development – custom software development involves developing a concept and building a solution from scratch. As a result, if incorrect assumptions are made in the system design and development process, there may be security vulnerabilities in the final product.
2. Lack of appropriate testing and quality assurance – orders for custom software often result in complex systems that require extensive testing and implementation of appropriate quality assurance procedures under Quality Assurance and Quality Control. If these processes are not thorough enough, vulnerabilities may go undetected, leaving the system open to potential attacks.
3. Insufficient security measures – even if software is designed and developed in a secure manner, it still needs to be protected by appropriate procedures and technical security measures such as firewalls, intrusion detection systems and properly planned and enforced access controls.
4. Human Error – A data breach can also occur due to human error, such as accidentally sending confidential information to the wrong recipient or falling victim to a phishing scam.
5. Malware and Viruses – Malware and viruses can infect custom software just like any other type of software, potentially compromising sensitive information.
6. Third-Party Vulnerabilities – Custom software often relies on third-party components such as libraries or plugins that may have their own vulnerabilities.
To prevent data breaches when developing custom software, it is important to adopt a comprehensive approach to security that includes secure design and development practices, thorough testing and quality assurance processes, appropriate security procedures, as well as ongoing monitoring and maintenance.
Examples of custom software security solutions used by SOFTIQ
Thanks to many years of experience, we know that the development of custom software, due to its unique nature and potential weaknesses, is a process that requires the use of the best possible security measures and the implementation of appropriate practices within entire project teams.
At SOFTIQ, we attach particular importance to the security of the created software, which is why, among other things:
- we produce software in accordance with the principles of „security by design” and „security by default”,
- when developing software, we pay attention to the OWASP TOP 10 list,
- we periodically test our software using automatic vulnerability scanners,
- we have our own security testers,
- we participate in conferences of the IT Security industry,
- we apply good security practices in version control systems.
SOFTIQ case study – an example of care for software security as part of the maintenance and development services of the information system for a local Ministry

SOFTIQ, under the agreement signed in 2020 with the Ministry, is responsible for 48 months for:
- system development,
- administration,
- removing failures and errors,
- user support,
- provision of hotline service.
In the course of work within the information system, SOFTIQ is obliged to strictly comply with the provisions of the Information Security Policy in the IT area implemented by the Ministry, which regulates a number of issues supporting the process of managing the IT infrastructure of the Ministry.
Some of the system security requirements that SOFTIQ is required to comply with include:
- applying the principle of password complexity to the system, its periodic change and protection against disclosure,
- in the case of the first login, forcing a change of the password assigned by the administrator,
- specifying the session activity time, after which the system is disconnected and access to it requires re-logging,
- using the functionality of remembering the last 5 passwords, preventing their reuse,
- observing the principles of safe storage of the system source code,
- the requirement to separate the production environment from other environments and comply with the ban on conducting development work in this environment,
- the obligation to continuously monitor the efficiency and safety of the system components,
- monitoring data growth, the amount of free disk space and the length of the current backup window.
What other software security practices should be followed in the work of development teams?
Among the various ways to ensure the security of custom software, often of varying effectiveness, SOFTIQ specialists can recommend the use of the following solutions:
1. Threat modeling.
Threat modeling is the process of identifying potential security threats and application vulnerabilities. This practice helps developers design and implement security controls that protect against potential attacks.
2. Secure coding practices.
Secure coding practices include the use of coding techniques that minimize the risk of application vulnerabilities. Examples of secure coding practices include input validation, error handling, and secure data storage.
3. Authentication and authorization.
Authentication and authorization are critical security measures that ensure that only authorized users can access specific functions or data in an application or system. Developers should implement strong access authentication and authorization controls to prevent unauthorized access.
4. Encryption.
In the created custom software, strong encryption algorithms should be used to protect data, both during its transmission and storage.
5. Access control.
Access control is the practice of limiting users’ access to specific resources in an application. Developers should implement granular access controls to limit user privileges and prevent unauthorized access.
6. Audit and Activity Recording.
Auditing and logging are core security practices that help developers monitor system activity and detect potential security threats. Developers should implement logging mechanisms that capture relevant information such as user activity, system events, and error messages.
7. Security testing.
Security testing is the process of assessing the effectiveness of implemented security controls in the application. Developers should conduct regular security tests to identify vulnerabilities and ensure that the implemented mechanisms work as intended.
8. Update management.
Patch management is the process of developing and deploying updates or patches to applications to address known vulnerabilities. Developers should develop and maintain a patch management process to ensure that applications are up to date with the latest security standards.
9. Protection against vulnerabilities from third-party libraries.
Third-party libraries can introduce security vulnerabilities into applications. Developers should carefully evaluate third-party libraries before using them in custom software to ensure they are safe and up-to-date.
10. Safety training.
Security training is a critical practice that helps developers understand security risks and best practices for developing secure applications. Developers should undergo regular security training to stay up to date with the latest threats and know how to protect themselves against them.
Benefits of secure development of custom software
Only a comprehensive approach to secure development of custom software, including appropriate procedures at every stage, from design, through programming, testing and further system maintenance, ensure that the software is protected against cyberattacks and data breaches.
The benefits of secure software development include:
- reduced risk of data breaches – by identifying and eliminating potential vulnerabilities at an early stage of the system development process, the likelihood of exploiting vulnerabilities by attackers to gain unauthorized access to sensitive data is reduced,
- increased customer trust – Customers are more likely to trust companies that prioritize security in their custom software development processes. By implementing secure software development practices, companies can demonstrate their commitment to protecting customer data and maintaining their privacy,
- cost saving – patching vulnerabilities after product release is costly and time consuming. By emphasizing the security of the custom software development process from the outset, companies can save money by avoiding costly remediation later.
Other benefits of secure software development include better compliance with industry regulations and reduced system downtime due to security incidents.
Summary
As we have emphasized several times, the process of creating a custom software includes developing a concept and building a solution from scratch. As a result, if incorrect assumptions are made in the system design process, security vulnerabilities may exist in the final product.
Appropriately designing a modern and safe system without appropriate experience may be impossible in many cases. In this context, often the best way to reduce risk and ensure the highest level of security is to choose the right software house that will take care of the optimal execution of your order.
Regardless of the type of software or application you want to create, the decision to choose a specific software house will be of key importance and will translate into every aspect of future cooperation, both in financial and organizational terms.
If you are wondering how to approach the choice of a partner and what to pay attention to, we encourage you to contact our consultant or read our articles – „How to choose the best software house for your project” – part 1 and part 2.








